Duration: minimum 2.5 hours
People: 1-2 facilitator(s), ± 6 participants
Materials: Paper, pen, whiteboards, sticky notes
Workshop Description
Many factors might prevent potential grantees from applying to a funding program, even if they seem like a perfect fit based on the eligibility criteria. This workshop helps people from different teams within a funding organization to identify those risk factors and gain a better understanding of their target grantee groups.
Objectives
The aim of this workshop is to bring the team together to:
- Define the target grantee(s)
- Develop a shared understanding of the major risks and threats facing applicants
Participation Guidelines
Participants are encouraged to:
- Ask clarifying questions at any time, but save open questions for the discussion
- Write opinions freely in silent individual activities
- Say opinions freely in group activities
- Mute themselves
ifduring the silent individual activities - Write in the chat when a break is needed (no need to announce it)
Workshop Possible Activities
1. Who is your ideal grantee?
In this exercise, you will write a profile of an imaginary grantee who is an especially good fit for your funding program – the kind of grantee who you might meet and instantly think, “perfect, we can’t wait to support you!” Not everyone on your team may agree, and that’s okay; the point of this exercise is not only the finished template but also the conversations that you have during the activity.
Have you already defined your ideal grantee? Unless you just did it yesterday, this exercise is likely useful anyway; it may bring up aspects of these profiles that you haven’t thought of, or it may be a good chance to hear the perspectives and questions of team members who weren’t present for the original conversation.
Note: If your team has already defined your target grantees, use the dedicated time for this activity to revise your personas and/or add personas that would belong to the stress-cases / risk groups.
- A stress case is when an aspect of a persona or a context is pushed to an extreme. Learn more about stress cases here.
Instruction: See Draw Your Ideal Grantee

2. Threat Modelling
“Threat modeling” is the term used in the security community for proactively thinking through the possible risks and harms to a person in order to keep them safe. “Harm” and “risk” may seem like strong words to use in the context of funding, but consider that grantees are giving you a great deal of information they would not publicly disclose, and are thus putting a lot of trust in you. Your actions determine the well-being and livelihoods of grantees and/or the people they support. This exercise will help you figure out where these potential harms lie.
In this exercise, you’ll use the profile from Exercise 1 and apply the template below to think through their thoughts and actions. Consider “explicit” needs, wants, risks, and actions to be things that they would freely tell you, and “implicit” to be things that are understood but not spoken aloud.
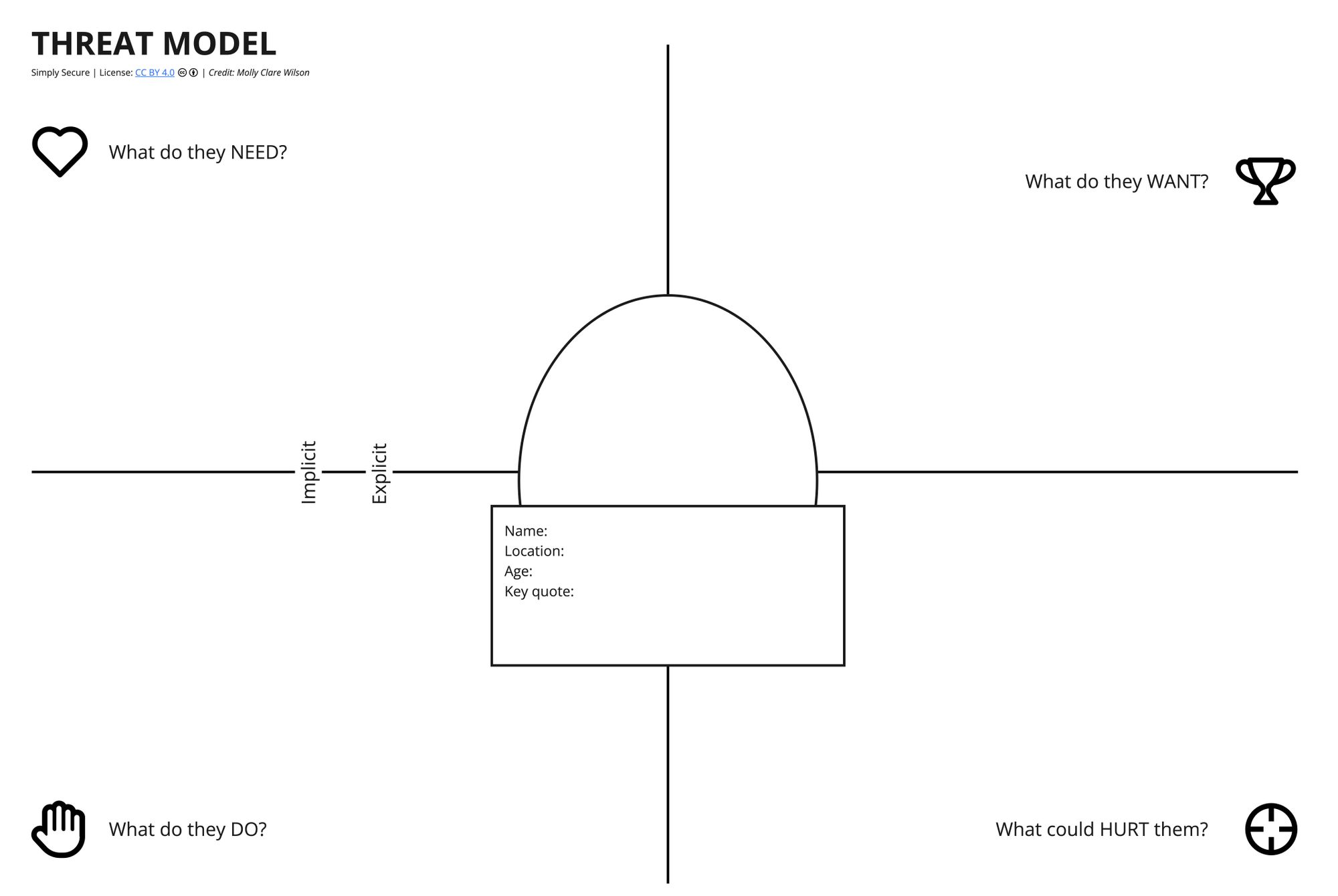
Instruction:
- Divide your group into breakout rooms if there are more than 4 or 5 people present.
- Talk through your assigned persona — give them a name, age, and location.
- Fill out the board by copy + pastings or drag post-its to the category that corresponds to your idea. Use virtual post-its or text blocks to fill out the fields in the template together.
- Evaluate the risks your funding process would pose to the participants.
Risks can mean (but aren’t limited to):
- Risk of personal data leaking
- Risk of research content leaking
- Risk of association with the application form/funding
- Risk of association with stakeholders involved
- Risk of applicants knowing about each other
3. Threat Down
If the last exercise helped you see possible risks and threats to a particular type of grantee, this exercise helps you understand all the risks and threats that different grantees may encounter. Go into this activity with an open mind, willing to talk about fears that may at first seem overblown or overly specific to you, and willing to learn about dangers others experience that may be new to you. Do not minimize or dismiss any risks that come up; simply write them down, and you can evaluate their likelihood later.
Threat Down is a "game" that helps explore threats and surface collective expertise and experience. It consists of 3 parts:
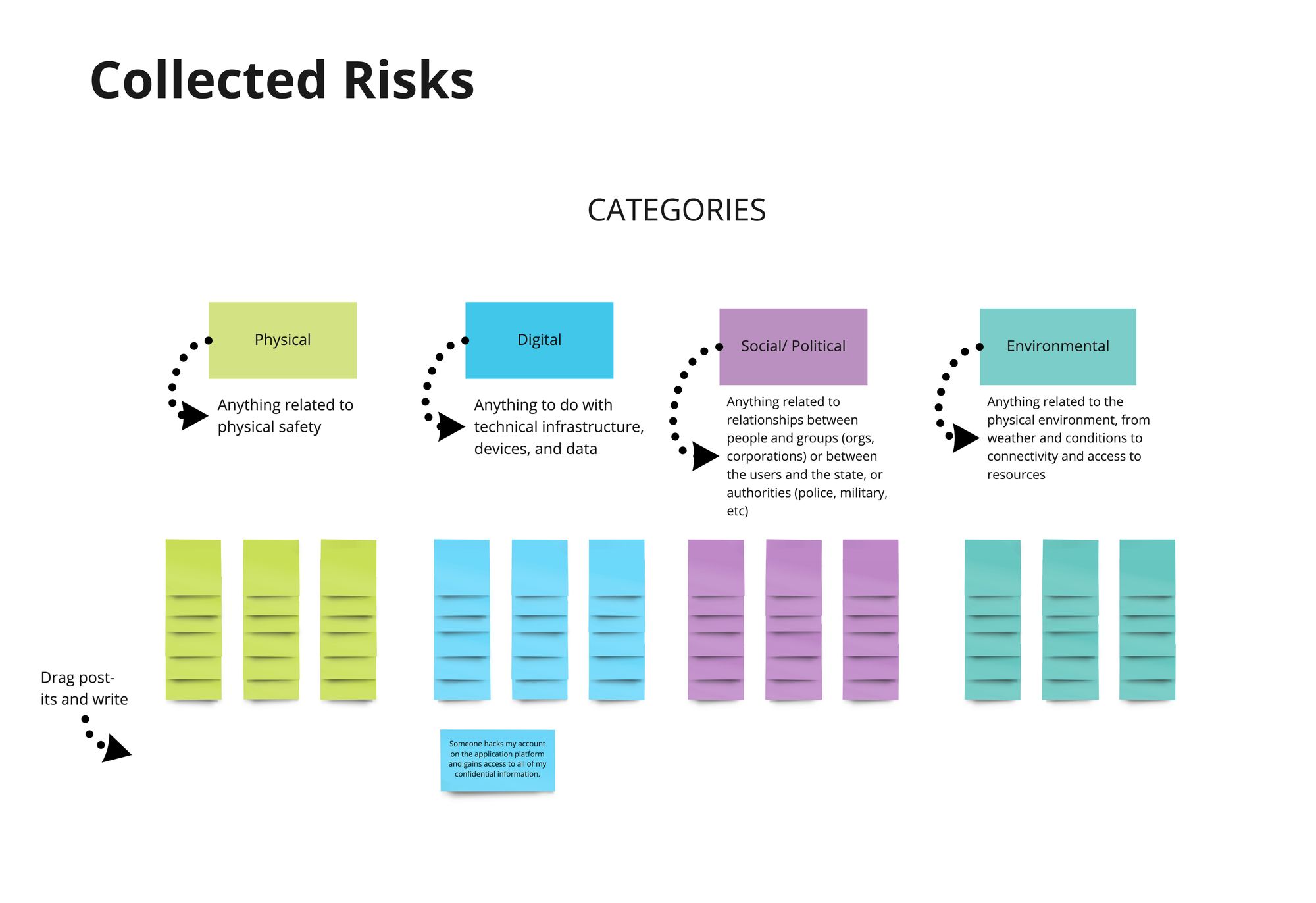
Part 1: Collected Risks
There are four categories of risks:
Group 1: Physical — Anything related to the physical safety
Group 2: Digital — Anything to do with technical infrastructure, devices, and data
Group 3: Social/Political — Anything related to relationships between people and groups (organizations, corporations) or between people and state authorities such as police and military the users and the state, or authorities (police, military, etc)
Group 4: Environmental — Anything related to the physical environment, from weather and conditions to connectivity and access to resources
Instruction:
- Working individually, think of a risk
- Example: Someone hacks my account on the application platform and gains access to all of my confidential information.
- Copy + paste or drag a post-it to the category that corresponds to your idea
- Assign it a number from 1-6 (where 1 is least likely to happen and 6 is most likely to happen)
- Repeat for more risks
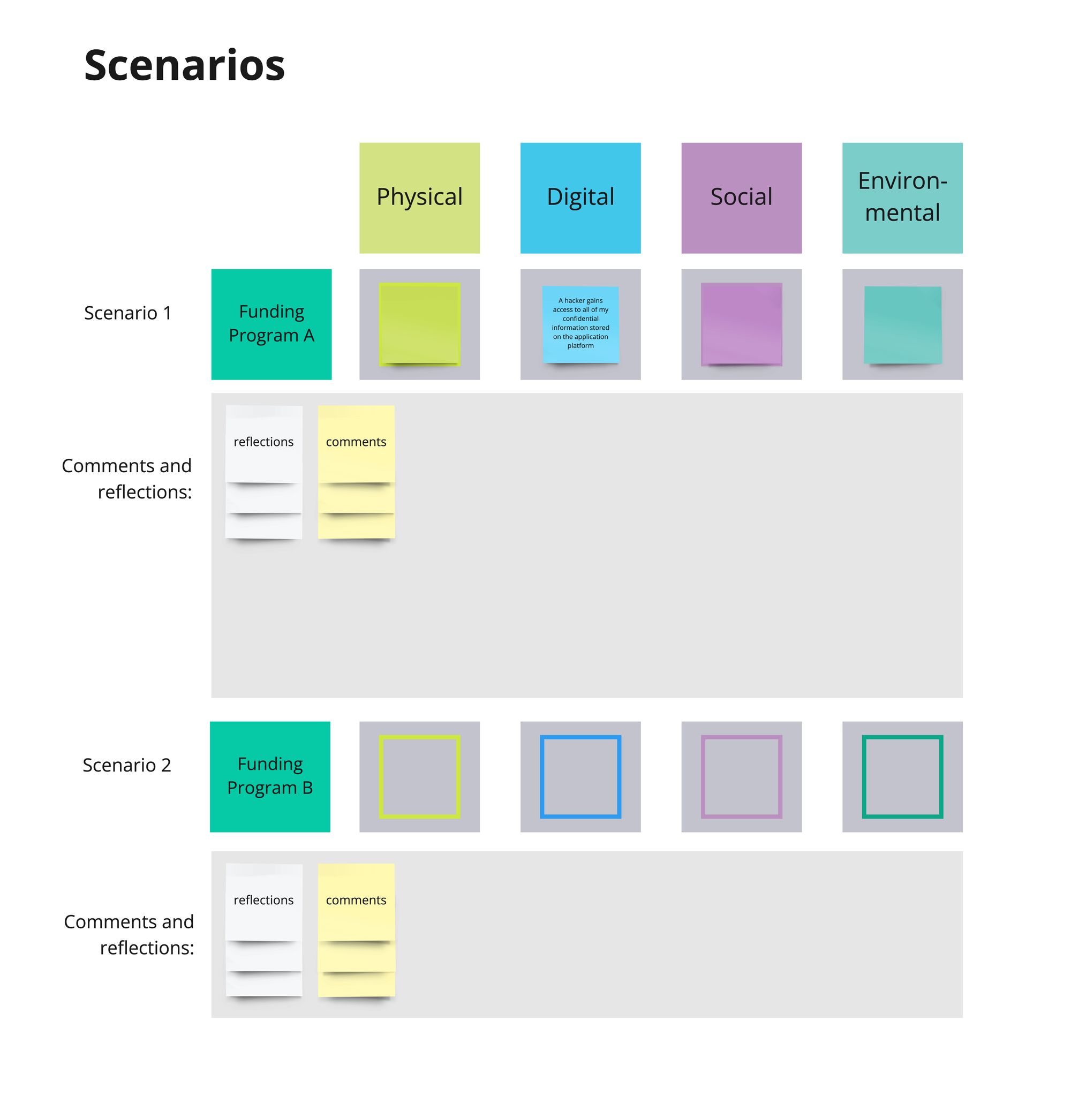
Part 2: Scenarios
Instruction:
- Roll the dice 4 times (once for each category) to build a scenario
- Discuss and reflect on the scenario:
- What would you do in this situation? How could you mitigate these risks? (these seem to me to be the much more interesting questions, no?)
- Collect reflections and comments, and gather them under the scenario
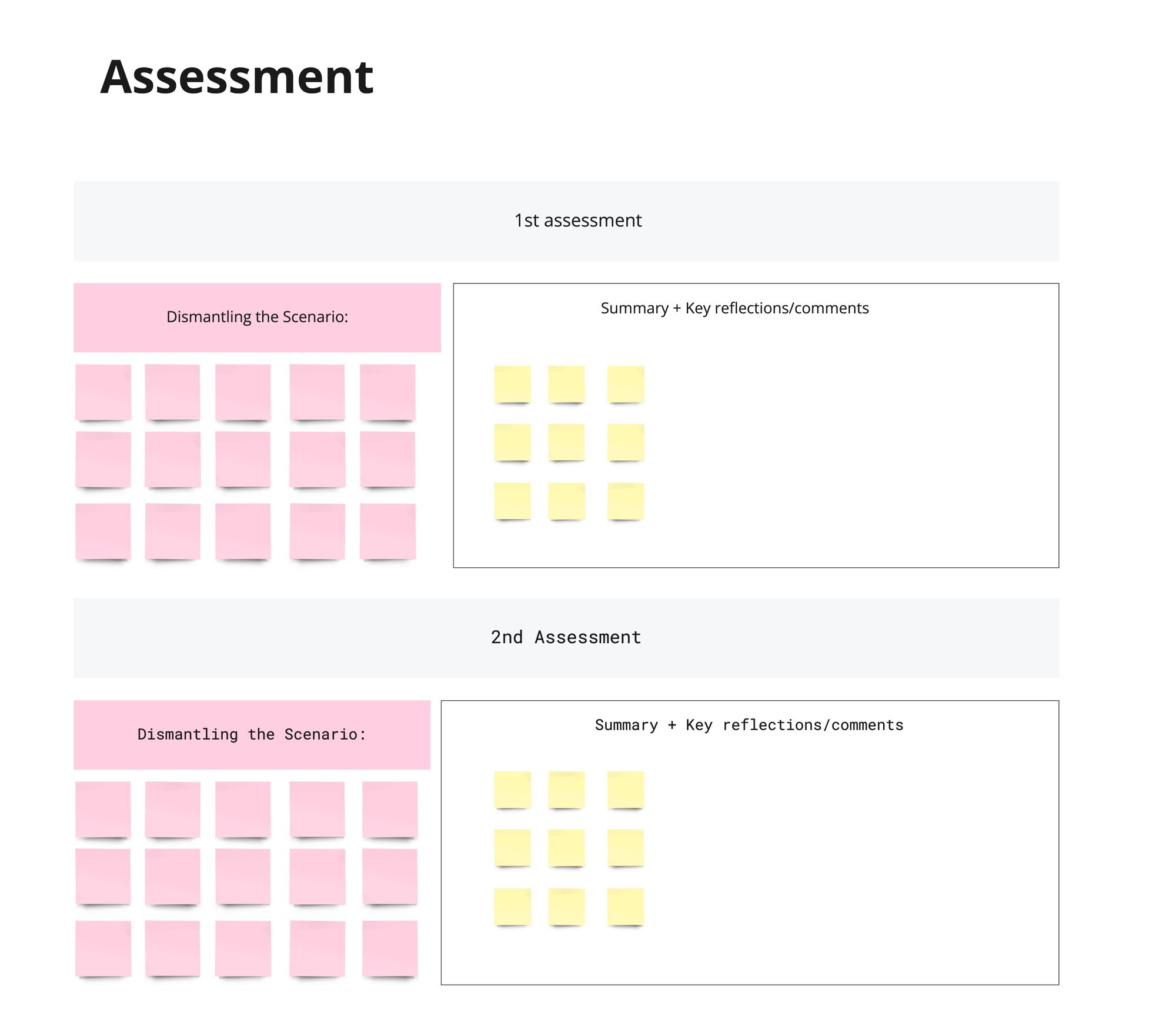
- After reflecting on the scenario, dismantle it. Discuss as a group what you could do to 1) De-escalate the scenario or risk within the scenario, or 2) Neutralize a risk or mitigate the second-order effect of one anxiety to another.
- Build an "assessment" of the scenario: Summarize the key reflections, comments, and ways of dismantling the scenario.
Workshop Sample Agenda
AM
9:00 - Introduction & Housekeeping
9:15 - Check-in: “What are you hoping to get out of this workshop?”
10:20 - Activity #1 “Draw Your Ideal Grantee(s)"
10:40 - Activity #1 Results Discussion and Feedback
11:00 - Activity #2 “Threat Modelling"
11:30 - Activity #2 Results Discussion & Feedback
11:45 - Break (15 minutes)
12:00 - Activity #3 “Threat Down"
PM
12:45 - Activity #3 Results Discussion & Feedback
1:00 - Closing & Feedback